Podman - a daemon-less docker alternative
Posted in development on November 13, 2020 by Adrian Wyssmann ‐ 6 min read
Podman is a daemonless container engine for developing, managing, and running OCI Containers on your Linux System. Containers can either be run as root or in rootless mode.
We have seen what is Docker and we also have seen that docker requires a daemon to be running
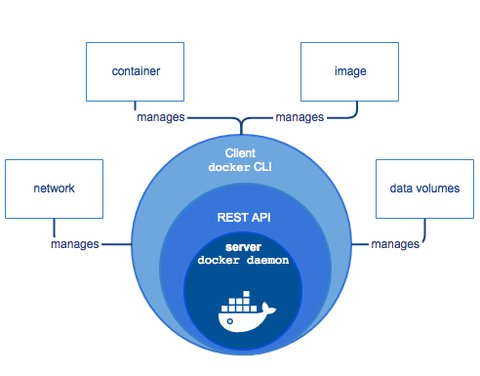
So the docker daemon is a central point of failure, cause if the docker daemon fails to run, your containers will as well. So here comes Podman
What is Podman
Podman is a daemonless container engine for developing, managing, and running OCI Containers on your Linux System. Containers can either be run as root or in rootless mode.
It offers basically the same as docker plus some things more
- Support multiple image formats including the OCI and Docker image formats.
- Support for multiple means to securely download images including trust & image verification.
- Container image management (managing image layers, overlay filesystems, etc).
- Full management of container lifecycle.
- Support for pods to manage groups of containers together.
- Resource isolation of containers and pods.
They use the same command set as docker cli so you can simply create an alias alias docker=podman. Installation is simple as it is available for the most linux distribution, Mac OS and also Windows. However, the downside for Windows is that
You can do this from a Windows desktop as long as you have access to a linux box either running inside of a VM on the host, or available via the network
Yeah in a corporate environment this might not be the case - I cannot install any virtual machine engine on my work computer nor do I have the latest Windows so I could potentially use [WSL]({{ ref “windows-subsystem-for-linux-wsl”>}}).
Let’s get started with rootless containers
On my Arch, I quickly install podman and then run a simple podman search multitool:
[adrian@archlinux]$ podman search multitool
INDEX NAME DESCRIPTION STARS OFFICIAL AUTOMATED
docker.io docker.io/psoders/multitool Just debug your docker environment 0 [OK]
docker.io docker.io/shaytan4/multitool multitool 0
docker.io docker.io/przemekmalak/multitool Multitool go server for testing https://git... 0
docker.io docker.io/thebwt/multitool How do I make this pool the github readme... 0 [OK]
docker.io docker.io/praqma/network-multitool A multitool for container network troublesho... 45 [OK]
docker.io docker.io/mantlpkg/multitool automatic builds and package tests for RPMs ... 0 [OK]
docker.io docker.io/rporres/multitool 0
docker.io docker.io/dhcgn/multitool Just a small toolbox I often need 0
docker.io docker.io/hoeghh/multitool 0
docker.io docker.io/nyvanga/multitool 0
docker.io docker.io/nyvanga/multitool-k8s 0
docker.io docker.io/sieger/multitool 0
docker.io docker.io/agalan75/multitool 0
docker.io docker.io/agregad/multitool 0
docker.io docker.io/woozymasta/network-multitool A multitool for container network troublesho... 0
docker.io docker.io/agorbatchev/network-multitool A multitool for container network troublesho... 0
quay.io quay.io/realeyes/alpine-node-video-multitool 0
quay.io quay.io/jhuddles/network-multitool .I am quite surprised - not only that it works - but that it does not only search docker.io but also quay.io, RedHat’s container registry. So let’s run a container:
[adrian@archlinux]$ podman run docker.io/praqma/network-multitool
ERRO[0000] cannot find UID/GID for user adrian: open /etc/subuid: no such file or directory - check rootless mode in man pages.
Trying to pull docker.io/papanito/cve-search...
Getting image source signatures
....
Copying blob df20fa9351a1 done
Copying config 3d7dc4b870 done
Writing manifest to image destination
Storing signatures
Error processing tar file(exit status 1): there might not be enough IDs available in the namespace (requested 0:42 for /etc/gshadow): lchown /etc/gshadow: invalid argument
Error: unable to pull docker.io/papanito/cve-search: Error committing the finished image: error adding layer with blob "sha256:171857c49d0f5e2ebf623e6cb36a8bcad585ed0c2aa99c87a055df034c1e5848": Error processing tar file(exit status 1): there might not be enough IDs available in the namespace (requested 0:42 for /etc/gshadow): lchown /etc/gshadow: invalid argumentBummer. Well checking the installation instructions which redirects me here, which does really help. So I digged deeper and found Basic Setup and Use of Podman in a Rootless environment. plus the following articles in Archlinux - Wiki:
- https://wiki.archlinux.org/index.php/Podman
- https://wiki.archlinux.org/index.php/cgroups#Switching_to_cgroups_v2
- https://wiki.archlinux.org/index.php/Kernel_parameters
In addition you may also read How does rootless Podman work? to understand why certain things are needed.
Apparently there are some things required in order for rootless containers to work, so let’s do it:
Ensure you enable
kernel.unprivileged_userns_clone=1. For me it’s already enabled$ sudo sysctl kernel.unprivileged_userns_clone kernel.unprivileged_userns_clone = 1If it’s not you can enable it by running
sudo sysctl kernel.unprivileged_userns_clone=1or permanently by adding it to/etc/sysctl.d/userns.confEnable cgroups v2 - which is enabled in Arch but default systemd mounts cgroup v1. I enabled it manually as follows for now:
mount -t cgroup2 none /sys/fs/cgroupDownload
crunas The default runtimeruncdoes not currently work with cgroup V2 enabled systems, so you have to switch to the alternative OCI runtimecrunsudo pacman -S crunRootless Podman requires the user running it to have a range of UIDs listed in
/etc/subuidand/etc/subgidfiles. As these do not exist, I have to create themsudo touch /etc/subuid /etc/subgidAs you recently created the empty files, you also have to create ids for
subuidsandsubuidsto be used:sudo usermod --add-subuids 100000-101000 --add-subgids 100000-101000 adrianAt least we run the migrate command as Github Issue #3421
podman system migrate
So let’s see again…
[adrian@archlinux]$ podman run docker.io/praqma/network-multitool
Trying to pull docker.io/praqma/network-multitool...
Getting image source signatures
Copying blob df20fa9351a1 done
Copying blob 121074dff36d done
Copying blob 4c26ad15482b done
Copying blob 32a58d9402d8 done
Copying blob a6f60c09bbc6 done
Copying config 3d7dc4b870 done
Writing manifest to image destination
Storing signatures
The directory /usr/share/nginx/html is not mounted.
Over-writing the default index.html file with some useful information.
Device "eth0" does not exist.Yeah, seems container started successfully, let’s check with podman ps
[adrian@archlinux]$ podman ps
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
a7d3737246a2 docker.io/praqma/network-multitool:latest nginx -g daemon o... 36 seconds ago Up 34 seconds ago adoring_lumiereLet’s also see if network connectivity works from the pod outside:
[adrian@archlinux]$ podman exec -it adoring_lumiere /bin/bash
bash-5.0# ping google.com
PING google.com (172.217.168.46) 56(84) bytes of data.
64 bytes from zrh04s14-in-f14.1e100.net (172.217.168.46): icmp_seq=1 ttl=255 time=11.3 ms
64 bytes from zrh04s14-in-f14.1e100.net (172.217.168.46): icmp_seq=2 ttl=255 time=14.4 ms
^C
--- google.com ping statistics ---
2 packets transmitted, 2 received, 0% packet loss, time 1002ms
rtt min/avg/max/mdev = 11.264/12.841/14.419/1.577 ms
bash-5.0#So running single containers is - as soon as your machine’s requirements are set - quite straightforward, especially when you already know docker commands.
Plugins
One nice thing is that docker has a plugin api which seems not be the case for Podman.
docker-compose with podman
So far this looks promising as a valid alternative of docker but what about the functionality which docker-compose brings to you
Compose is a tool for defining and running multi-container Docker applications. With Compose, you use a YAML file to configure your application’s services. Then, with a single command, you create and start all the services from your configuration.
Uninstalling docker from your system obviously also removes docker-compose. There seems to be a project “podman-compose” in github which tries to tackle this. However, as of today, This project is still under development.
I will give it a change and will create a separate post concerning this.