How to rescue data from windows
Posted on March 13, 2021 by Adrian Wyssmann ‐ 3 min read
My son has a Surface Go Tablet which suddenly stopped booting. Even after trying to uninstall patches etc. I could not bring it back, so I decided to help him to get the data from the tablet, so he can use it.
What do we need?
So in order to rescue data you create a bootable usb-disk with a linux os and boot your Windows computer/tablet from it. However one has to be aware of two things:
- Bitlocker: Modern Windows devices are increasingly protected with BitLocker Device Encryption out of the box
- UEFI: Secure Boot prevents the OS from booting unless they’re signed by a key loaded into UEFI - so per-default means only software signed by Microsoft
For the 1. issue, your Linux distribution of choice shall contain a tool to decrypt Bitlocker disks - for example dislocker. As distribution I recommend System-Rescue as it contains a nice set of default tools incl. dislocker. To decrypt the Bitlocker disks you also need the recovery key provided by Microsoft which looks something like XXXXXX-XXXXXX-XXXXXX-XXXXXX-XXXXXX-XXXXXX-XXXXXX-XXXXXX.
The 2. issue is a bit more challenging - or not, you have some options here
- Choose a Linux Distribution That Supports Secure Boot
- Disable Secure Boot
- Add a Signing Key to the UEFI Firmware
Disabling secure boot will remove the security benefits, but as I try to recover data, it really does not matter and guess is the easiest way to be able to boot the usb-disk.
Steps to recover the data
- First you have to download the
isoand then create a bootable usb-disk - On the Computer/Tablet enter the BIOS
- disable Secure Boot
- change the boot order so that the usb drive is before the internal disk
- Put the bootable usb-stick in the USB port and boot up your Linux distro
From there check which is the Bitlocker disk - I use Gparted, but you may also use fdisk or whatever you have at hand:
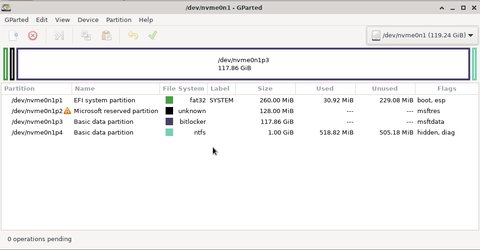
Once you have identified the disk you can go on and use [dislocker] to decrypt the disk. Ensure you have a mount point:
[root@sysrescue ~]# mkdir /mnt/disk
[root@sysrescue ~]# dislocker /dev/nvme0n1p3 -vvv -pXXXXXX-XXXXXX-XXXXXX-XXXXXX-XXXXXX-XXXXXX-XXXXXX-XXXXXX -- /mnt/disk/
Sat Mar 13 10:14:41 2021 [INFO] dislocker by Romain Coltel, v0.7.2 (compiled for Linux/x86_64)
Sat Mar 13 10:14:41 2021 [INFO] Compiled version: master:820c0f5
Sat Mar 13 10:14:41 2021 [INFO] Volume GUID (INFORMATION OFFSET) supported
Sat Mar 13 10:14:41 2021 [INFO] BitLocker metadata found and parsed.
Sat Mar 13 10:14:41 2021 [INFO] Stretching the recovery password, it could take some time...
Sat Mar 13 10:14:43 2021 [INFO] Stretching of the recovery password is now ok!
Sat Mar 13 10:14:43 2021 [INFO] Used recovery password decryption method
Sat Mar 13 10:14:43 2021 [INFO] Found volume's size: 0x1d77300000 (126553686016) bytes
Sat Mar 13 10:14:43 2021 [INFO] Running FUSE with these arguments:
Sat Mar 13 10:14:43 2021 [INFO] `--> 'dislocker'
Sat Mar 13 10:14:43 2021 [INFO] `--> '/mnt/disk/'So let’s see what we have under /mnt/disk
[root@sysrescue ~]# ls /mnt/disk
[root@sysrescue ~]# dislocker-fileNot what I expected - I thought the /mnt/disk/ contains the decrypted content mounted but instead it contains a dislocker-file. According to dislocker, it’s a flat file which can be mounted as NTFS partition. So, let’s mount it:
[root@sysrescue ~]# mkdir /mnt/bitlocker
[root@sysrescue ~]# mount /mnt/disk/dislocker-file /mnt/bitlocker/`Finally I have access to the data, so from there we can copy the data.
