Microsoft Azure: Security and Network Security
As part of the Microsoft Enterprise Skills Initiative I am looking into different topics in Azure and summarize my learnings. This post is about Azure Security and Network Security
Azure Security Center
Azure Security Center is a unified infrastructure security management system to see security relevant information for all your services in the cloud and on-premise. It has a free tier but certain feature have to be payed:
- Monitor security settings to identify and perform the hardening tasks recommended as security best practices and implement them across your machines, data services, and apps
- Automatically apply security policies on management groups, across subscriptions and for a whole tenant. For example you can have an application control rule, which enforces that only certain applications run on a particular VM.
- Provide security recommendations that are based on your current configurations, resources, and networks.
- Continuously monitor your resources and perform automatic security assessments to identify potential vulnerabilities before those vulnerabilities can be exploited.
- Use machine learning to detect and block malware from being installed on your virtual machines (VMs) and other resources. You can also use adaptive application controls to define rules that list allowed applications to ensure that only applications you allow can run.
- Detect and analyze potential inbound attacks and investigate threats and any post-breach activity that might have occurred.
- Provide just-in-time access control for network ports. Doing so reduces your attack surface by ensuring that the network only allows traffic that you require at the time that you need it to.
Azure Sentinel
Azure Sentinel is the security information event management (SIEM) and security orchestration automated response (SOAR) solution. It offers
- to connect to all your data using a connectors or use Syslog or REST-API to connect your data sources.
- View and analyse your data using Azure Monitor Workbooks
- analytics to correlate alerts into incidents i.e. groups of related alerts that together create an actionable possible-threat that you can investigate and resolve
- automate common tasks and simplify security orchestration with playbooks, which can interact with different services.
- tools for investigation of incidents including interactive graphs
- a powerful hunting search-and-query tools to proactively hunt for security threats across your data sources
Azure Key Vault
Azure Key Vault is a tool to help you keep sensitive information secure:
- Secret Management to securely store and tightly control access to tokens, passwords, certificates, API keys, and other secrets. It als
- Encryption Keys Management to easily create and control the encryption keys
- SSL/TLS Certificate Management to provision, manage, and deploy your public and private SSL/TLS certificates for cloud and on-premise resources
These secrets and keys can be protected either by software or by FIPS 140-2 Level 2 validated hardware security modules (HSM). For Kubernetes secrets-store-csi-driver-provider-azure my be interesting as it
allows you to get secret contents stored in Azure Key Vault instance and use the Secret Store CSI driver interface to mount them into Kubernetes pods.
Azure Dedicate Host
Azure Dedicate Host is a service that provides physical servers as a resource, on which you can host VMs. They belong to a specific region, availability zone, and fault domain. Benefits
- Hardware isolation at the physical server level, only your VMS run on it
- Deployed in same data centers and share the same network and underlying storage infrastructure as other, non-isolated hosts
- Opt-in to a maintenance window to reduce the impact to your service
- Use your own licenses
- Multiple servers can be grouped to a host group
Network Security
Azure Firewall managed, cloud-based network security service, to centrally create, enforce, and log application and network connectivity policies across subscriptions and virtual networks. You can monitor incoming and outgoing traffic and block traffic based on rules:
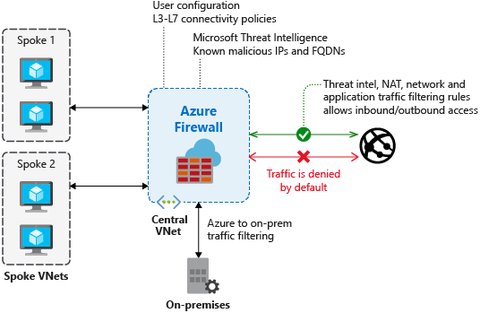
It includes the following features:
- Built-in high availability
- Availability Zones
- Unrestricted cloud scalability
- Application FQDN filtering rules
- Network traffic filtering rules
- FQDN tags
- Service tags
- Threat intelligence
- Outbound SNAT support
- Inbound DNAT support
- Multiple public IP addresses
- Azure Monitor logging
- Forced tunneling
- Web categories (preview)
- Certifications
With Azure Application Gateway you also have a web application firewall (WAF) that provides centralized, inbound protection for your web applications against common exploits and vulnerabilities.
Azure DDoS Protection offers protection against Distributed denial of service (DDoS) attacks with a free basic and a payed standard tier. The Basic service tier ensures that Azure infrastructure itself is not affected during a large-scale DDoS attack. The Standard tier provides additional measures to deal and prevent DDoS attacks.
Whereas Azure Firewall and Azure DDoS Protection are meant for outside sources, we also have Network Security Groups (NSGs) - as mentioned earlier in the post - which filter network traffic to and from Azure resources within an Azure virtual network.